Usability > Security
Introduction
The other day I wanted to use my noscript.it with one of my old iPhone 4S running iOS 6, but I was met with “could not establish a secure connection to the server”.
 Turns out it was because I had, out of habit, configured the server with a "modern" list of TLS ciphers. And the poor old iOS 6 didn't support any of them.
Turns out it was because I had, out of habit, configured the server with a "modern" list of TLS ciphers. And the poor old iOS 6 didn't support any of them.
So, I went on a mission to ensure noscript.it works with as old devices as possible.
It turns out enabling TLS1 and TLS1.1 on Ubuntu 20.04 is a bit harder than I expected1. Luckily someone else solved it already.
So now, after using the old mozilla SSL config and appending @SECLEVEL=1, it works. Even on my vintage iPhone 3G. Hurray!
 ### Wait what?
**But**, I hear you say, isn't this less secure? I mean now you only get a **B** [on the Qualys SSL Report](https://www.ssllabs.com/ssltest/analyze.html?d=noscript.it&hideResults=on)! Clearly this is **bad**!?
### Wait what?
**But**, I hear you say, isn't this less secure? I mean now you only get a **B** [on the Qualys SSL Report](https://www.ssllabs.com/ssltest/analyze.html?d=noscript.it&hideResults=on)! Clearly this is **bad**!?
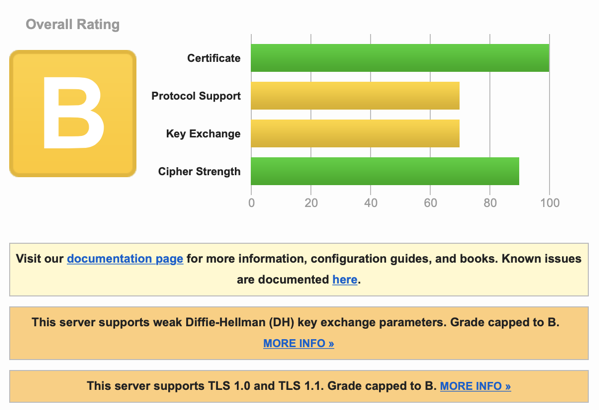 Let’s take a step back and think about what the score actually means. noscript.it automatically gets a B because it supports TLS1. But let’s go one step further and assume we’re looking a bank with a C2. A site gets a C if it supports SSLv3, meaning it is vulnerable to the SSLv3 POODLE3 attack. This is clearly bad for a bank!? Or is it? How likely is it that someone will successfully execute this attack, which requires the attacker to have the ability to intercept and modify the data transmitted. And compare this likelihood with how likely is it that someone will need to access the bank website from an old XP (pre-SP3) machine only supporting SSLv3? The second seems more likely to me.4
Let’s take a step back and think about what the score actually means. noscript.it automatically gets a B because it supports TLS1. But let’s go one step further and assume we’re looking a bank with a C2. A site gets a C if it supports SSLv3, meaning it is vulnerable to the SSLv3 POODLE3 attack. This is clearly bad for a bank!? Or is it? How likely is it that someone will successfully execute this attack, which requires the attacker to have the ability to intercept and modify the data transmitted. And compare this likelihood with how likely is it that someone will need to access the bank website from an old XP (pre-SP3) machine only supporting SSLv3? The second seems more likely to me.4
Okay, you say, but won’t keeping SSLv3 around make everyone vulnerable because of downgrade attacks? If that were the case, the risk calculation would be different. But luckily, we have TLS_FALLBACK_SCSV to avoid that. TLS_FALLBACK_SCSV ensures that modern client and browser won’t risk being fooled to downgrade its encryption.
Conclusion
So to wrap things up, don’t stare blindly at the rating or certification. A site with A++ is more secure than one with a C rating. But if you (or someone less fortunate) can’t access the site when they need it, it will be a pretty useless site. Personally, from now on, unless the site needs 5 absolute security, all my projects will optimise for compatibility rather than getting an A++. After all, it is much more likely someone will try using it with a Windows XP or old Smart-TV compared to someone MITM-ing that person at that moment.
Disclaimer
Please note though, don’t read this as an argument against doing things securely as default and following best practices. Rather it is just some thoughts on this specific issue of TLS and SSL configurations. If you break with best practice, make sure you understand the reason why it’s best practice to begin with and what risks or weaknesses you introduce by not following them.
-
I 100% support secure defaults, make it hard to do the wrong thing. ↩︎
-
A favourite hobby of some people in the security community is to publicly shame banks or websites for not getting a great grade in the Qualys SSL test. Here is an example from Troy Hunt ↩︎
-
SSLv3, not to be confused with the POODLE attacks against some weak TLS implementations. ↩︎
-
Also there are mitigations which you should of course implement unless it breaks more than it fixes. ↩︎
-
in some cases, like highly sensitive data or targeted users the risk calculation will be different, it might be better for a user not to be able to use the site rather than risk some known (or unknown) attack. ↩︎