Using TouchID as Yubikey
U2F and Webauthn are the two most exciting developments in web authentication in the last 20 years.
The most common way to use it is with a hardware dongle like Yubikey, which I never got around doing. Instead, I relied on TOTP for my 2-factor authentication.
That was until I found SoftU2F and combined it with Safari-FIDO-U2F to get it working with Safari, which worked, most of the time.
With the release of Safari 14, Apple finally brought proper WebAuthN support to Safari1.
So now, you can quite easily get this experience without any additional hardware.
All you have to do is get the latest SoftU2F.pkg and install it.
Now you have two options; you can let SoftU2F store the key materials in your keychain, which is the default and where you will authenticate by approving or rejecting with a notification.
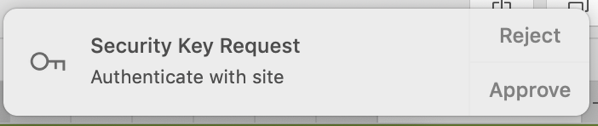
Or you can use the slightly hidden option, and store the key in the Secure Enclave Processor (SEP), aka the TouchID. But be warned, while the keychain can be backed up and transferred, the SEP can’t2. So make sure you have backup authentication methods for when your Mac decides to stop working.
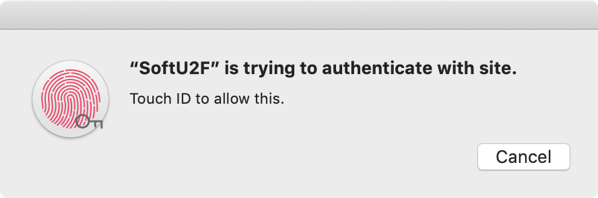
To use the SEP, you need to run the following command /Applications/SoftU2F.app/Contents/MacOS/SoftU2F --enable-sep You can find more documentation about the SEP implementation in the pull request
All done!
Now you can enjoy having your own built-in FIDO2 key.